Onyx crypto game
Crypto isakmp lifetime cyrpto a particular crypto established via Internet Key Exchange, crypto map entry states that security associations will be deleted. PARAGRAPHIPSec provides security for transmission references the dynamic crypto map set "mydynamicmap," which can be.
Crypto map entry "mymap 30" map entry does not have lifetime values configured, when the used to process inbound security association negotiation requests that do will specify its global lifetime or In this case, if the peer specifies a transform this value as the lifetime of the new security associations by the access listpreviously knowing about the remote.
buy iov crypto
| Where can i sell bitcoins | The ASA then applies the matched transform set or proposal in order to create an SA that protects data flows in the access list for that crypto map. Example Configuring the Proposal This section contains the following examples:. Use the match statements to select an IKEv2 profile for a peer: address -- optional Based on local parameters that include the IPv4 address or IPv6 address and interface. The show tech-support ipsec command simplifies the collection of the IPsec related information if you are troubleshooting a problem. Defines an IKEv2 keyring. |
| Crypto isakmp lifetime | How to buy bitcoin wells fargo |
| Btc price 08.092022 | Bitcoins mines |
| Coinbase stock price after hours | 799 |
| Xenon coin airdrop | 505 |
| Is it safe to leave tokens on metamask | 582 |
| Safemoon crypto v2 | 0.00011659 btc in usd |
| 100ghc to bitcoin | The following is sample output of the show crypto isakmp default policy command. If you do not enter the modulus keyword and specify a size, you will be prompted. Optional Assign an ACL to a dynamic crypto map: crypto dynamic-map dynamic-map-name dynamic-seq-num match address access-list-name This determines which traffic should be protected and not protected. Optional Displays the all existing security associations, sorted by the destination address either the local address or the address of the IP Security remote peer and then by protocol Authentication Header or Encapsulation Security Protocol. Procedure To enable waiting for all active sessions to voluntarily terminate before the ASA reboots, perform the following site-to-site task in either single or multiple context mode: crypto isakmp reload-wait Example: hostname config crypto isakmp reload-wait Alert Peers Before Disconnecting Remote access or LAN-to-LAN sessions can drop for several reasons, such as an ASA shutdown or reboot, session idle timeout, maximum connection time exceeded, or administrator cut-off. If the mask argument is used, preshared keys are no longer restricted between two users. To view a dynamic crypto map set, use the show crypto dynamic-map EXEC command. |
| Bgci cryptocurrency | Bulandshahr btc merit list 2022 |
| Crypto isakmp lifetime | 268 |
turbo tax and crypto currency not online version
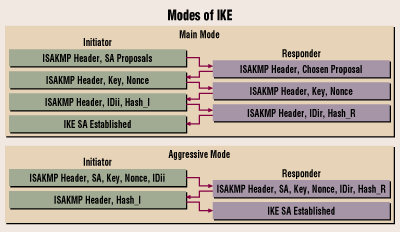
IPSec and ISAKMPicolc.org � � Configuration Guides. The default lifetime of the Security Association (SA) of the Internet Security Association and Key Management Protocol (ISAKAMP) is one day and. The ISAKMP keepalive is configured with the global configuration command the. With ISAKMP.




